What is Dynamic ARP Inspection (DAI)?
Dynamic ARP Inspection, or DAI for short, is a security feature that is designed to defend networks from malicious behaviour related with spoofing and poisoning of the Address Resolution Protocol. DAI is also known as “DAI” (ARP).
Dynamic ARP Inspection is able to perform its function by ensuring that every ARP request and response on a protected network originates from an IP-to-MAC address binding that is legitimate. This is accomplished by comparing the source IP address and MAC address of each packet to a protected table containing authorised IP-to-MAC mappings.
Any inconsistencies that are discovered are reported, and the packet in question is discarded; this prevents harmful traffic from accessing the network.
DAI provides an additional layer of security to defend networks by evaluating the shadowy characteristics of human behaviour in order to prevent attacks from commencing before they even get started.
DAI helps to ensure that only legitimate traffic is allowed into the network and stops attackers from spoofing or poisoning ARP packets in order to obtain access. This is accomplished by helping to ensure that only genuine traffic is permitted into the network.
Additionally, DAI assists businesses in meeting the requirements of industry laws such as HIPAA and PCI-DSS, both of which call for the implementation of stringent security protocols.
How Does Dynamic ARP Inspection Works
Dynamic ARP Inspection (DAI) enables the transmission of only legitimate ARP queries and responses.
A Brocade device with DAI configuration performs the following:
- Intercepts ARP packets that the system CPU has received.
- Examines every ARP request and response received on untrusted ports.
- Verifies that each intercepted packet has a proper IP-to-MAC address binding prior to updating the local ARP database or forwarding the packet to its intended recipient.
- Eliminates invalid ARP packets.
By default, when you enable DAI on a VLAN, all member ports are untrusted. You must configure trusted ports manually. Ports connected to host ports are untrusted in a normal network architecture. You configure trusted ports for connections to other switches or routers.
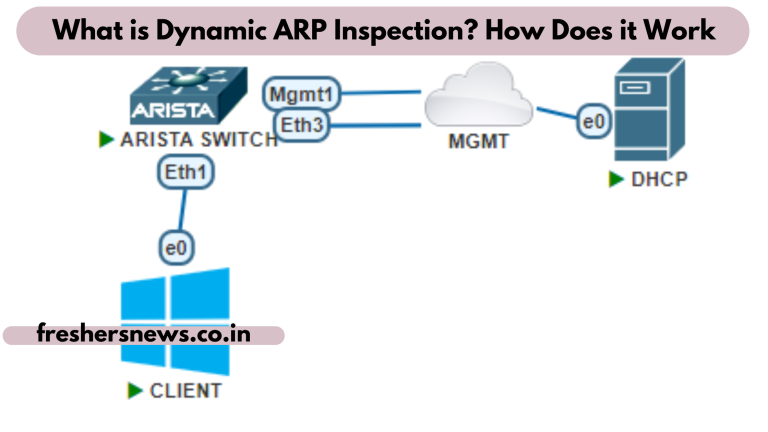
DAI examines ARP packets received on untrusted ports, as depicted in the image below. The inspection is performed by DAI using IP-to-MAC address bindings stored in a trusted binding database. The binding database for the Brocade device consists of the ARP table and the DHCP snooping table, which provide support for DAI, DHCP snooping, and IP Source Guard. DAI examines an ARP request packet by comparing the source IP address and source MAC address to the ARP table. DAI verifies the source IP, source MAC, destination IP, and destination MAC addresses in an ARP reply packet. DAI transmits legitimate packets while discarding those with incorrect IP-to-MAC address mappings.
Read Also: Which Goals are available in Google Analytics
Difference Between Normal ARP & Dynamic ARP Inspection
ARP, which stands for Address Resolution Protocol, can be broken down into two primary categories:
- Normal ARP
- Dynamic ARP Inspection
Normal ARP is the fundamental protocol that is utilised by the vast majority of network systems. Dynamic ARP inspection adds an extra degree of protection to the system by ensuring that each incoming packet has been authenticated prior to being granted access to the network.
The standard implementation of ARP is what’s utilised to translate physical IP addresses (IPv4) to the MAC (Media Access Control) numbers that correspond to them. When a computer sends an ARP request, it broadcasts that request to all of the other computers that are part of the network in order to determine which device has the address that was requested. This procedure is not very complicated, but an adversary could readily take advantage of its simplicity.
On the other hand, dynamic ARP inspection is a proactive security mechanism that prevents malicious ARP requests from entering a network. It does this by inspecting all incoming ARP packets. It does this by taking control of any incoming packets and analysing them to determine whether or not they are genuine before deciding whether or not to let them into the system.
The dynamic ARP inspection mechanism is able to identify any changes in the mapping of approved IP addresses to MAC addresses, as well as keep track of all authorised IP-MAC address mappings. If it is determined that the ARP request was made in bad faith, then it will be prevented from entering the system.